Windows Logon Type are logged in the Logon Type field of logon events. They are showing up in the windows security event log and reveal the type of logon that prompted the event.
In an Interactive logon, user enters credentials into the Log On to Windows dialog box or user inserts a smart card into the smart card reader. User’s authentication is then checked against the security database on the user’s local computer or to an Active Directory domain.
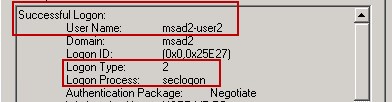
Windows Logon Type 2 – Interactive logon
Windows Logon Type 2 is used for a logon at the console of a computer. A type 2 logon is logged when you attempt to log on at a Windows computer’s local keyboard and screen whether with a domain account or a local account from the computer’s local SAM. To tell the difference between an attempt to logon with a local or domain account look for the domain or computer name preceding the user name in the event’s description.
Windows Logon Type 3 – Network logon
Windows Logon Type 3 are very common to Windows environment. They are only used after an account authentication such as user, computer, and service has already taken place. For network logon, the process does not use the initial logon dialog box to enter the credentials. Instead, already established credentials for the account are used, or credentials are collected using in a different way. This is typically invisible to the user unless alternate credentials are used. Network logon confirms the users’ identification to the network service such as mapped drive on another server that the user is attempting to access (Microsoft TechNet, 2003). Windows logs logon type 3 for network logons such as accessing shared folders, printers, GPOs, and most logons to IIS.
Windows Logon Type 4 – Batch logon
For a scheduled task execution in Windows, the Scheduled Task service first creates a new logon session for the task so that it can run under the user account specified for that task. Windows logs this logon attempt as logon type 4. Some job scheduling systems or other application, depending on their design, may also generate logon events with logon type 4
Windows Logon Type 5 – Service logon
Windows Logon Type 5 services are configured to run under specified user accounts individually. Starting of a service first creates a logon session for the specified user account which results in a Logon/Logoff event with logon type 5.
Windows Logon Type 7: Unlock
Logon Type 7 occurs when a user returns to the console and unlocks the password protected screen. Windows treats this as a logon and logs the appropriate Logon/Logoff event using logon type 7 identifying the event as an unlock attempt
Windows Logon Type 8
Windows Logon Type 8 is a kind of network logon where the password is sent over the network in the clear text. This is logged as logon type 8.Windows server doesn’t allow connection to shared file or printers with clear text authentication. It is possible with logons from within an ASP script using the ADVAPI or when a user logs on to IIS using IIS’s basic authentication mode. In both cases the logon process in the event’s description will list advapi authentication to authenticate to an IIS server.
Windows Logon Type 9: New credentials-based logon
Using RunAs command to start a program under a different user account with the /netonly switch, Windows records a logon/logoff event with windows logon type 9. When starting a program with RunAs using /netonly, the program executes on the local computer as the user currently logged on as but for any connections to other computers on the network, Windows connects to those computers using the account specified on the RunAs command. Without /netonly Windows runs the program on the local computer and on the network as the specified user and records the logon event with windows logon type 2
Windows Logon Type 10 – Remote Interactive logon
Windows Logon Type 10 is used for RDP-based applications like Terminal Services, Remote Desktop or Remote Assistance.
Windows Logon Type 11 – Cached Interactive logon
Windows Logon Type 11 feature facilitates mobile users that allow caching credentials hashes of the last 10 interactive domain logons by default. When client is off the network or when no domain controller is available, Windows uses these hashes to verify the identity of the logon with a domain account. It is logged with logon type 11
Conclusion
We hope this discussion of logon types and their meanings helps you as you keep watch on your Windows network and try to piece together the different ways users are accessing your computers. Paying attention to logon type is important because different logon types can affect how you interpret logon events from a security perspective.