A ransomware, is a malicious software that takes data hostage. A phishing email can be used to distributed them. It encrypts and blocks files contained on your computer including those shared on servers. You will lose access to these files and will have to pay a ransom to get them back. The purpose of the attack is to extort money (most often by virtual currency).
How to detect a ransomware?
They are usually hidden in a phishing email (with an attachment containing the virus or in a link that refers to a trapped site). They can sometimes take advantage of a System Vulnerability to install the virus autonomously on a workstation. There is no action to be done by the user. The tricks to detect them are the same as phishing email (see more here):
• The context of the e-mail is not plausible or the sender is not supposed to know the e-mail address of the recipient
• The sender’s address is unknown or suspicious
• The information requested is confidential: bank details, password…
• The tone of the e-mail is threatening or plays on empathy
• The e-mail contains spelling mistakes
Types of ransomware attacks
Two are the major themes where we can group:
- The ones who can lock you out of your computer, preventing you from logging on.
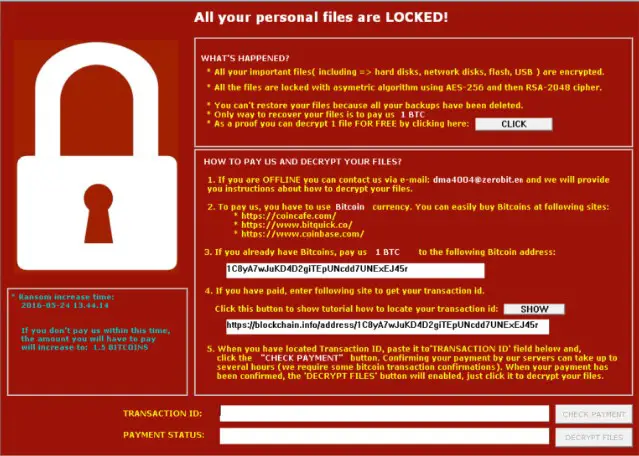
- The ones who encrypts your data files allowing you to log on but preventing you accessing any of your data.
The five types of ransomware are:
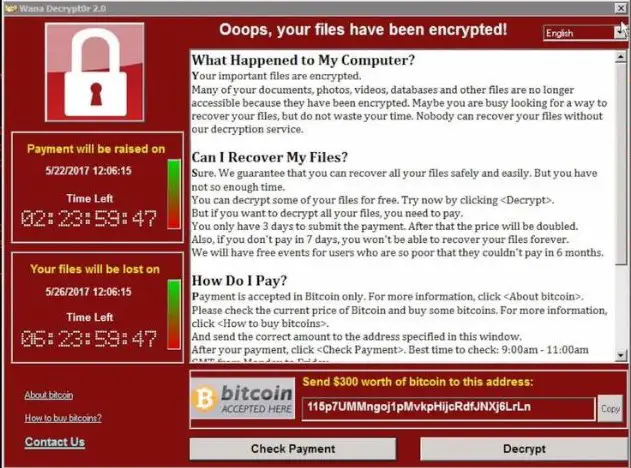
- Crypto. This is a well-known form of and can cause a great deal of damage. One of the most familiar examples is the 2017 WannaCry ransomware attack. It targeted thousands of computers around the world and spread itself within corporate networks globally. You can find more about it here
- Lockers. This kind is known for infecting your operating system to completely lock you out of your computer, making it impossible to access any of your files or applications.
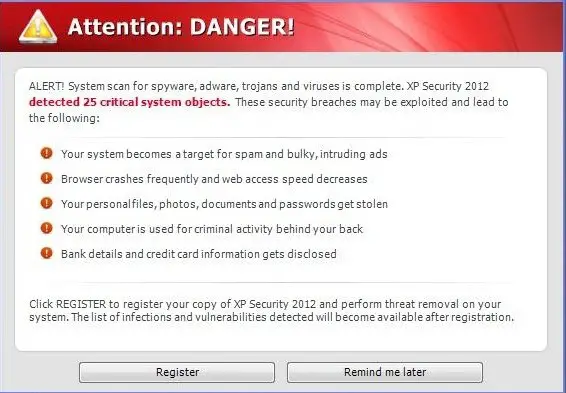
- Scareware. This is fake software that acts like an antivirus or a cleaning tool. Scareware often claims to have found issues on your computer, demanding money to resolve the issue. Some types of scareware lock your computer and other types flood your screen with annoying alerts and pop-up messages.
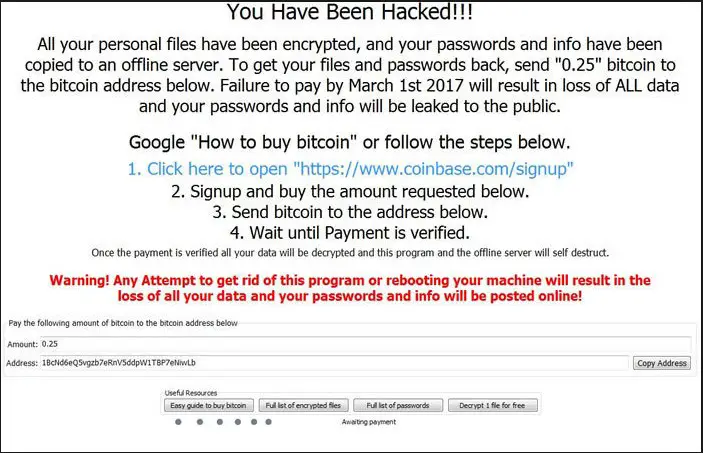
- Doxware. Commonly referred to as leakware, doxware threatens to publish your stolen information online if you don’t pay the ransom. People store sensitive files and personal photos on their computers. Many individuals will panic and pay the ransom if they find that their files have been hijacked
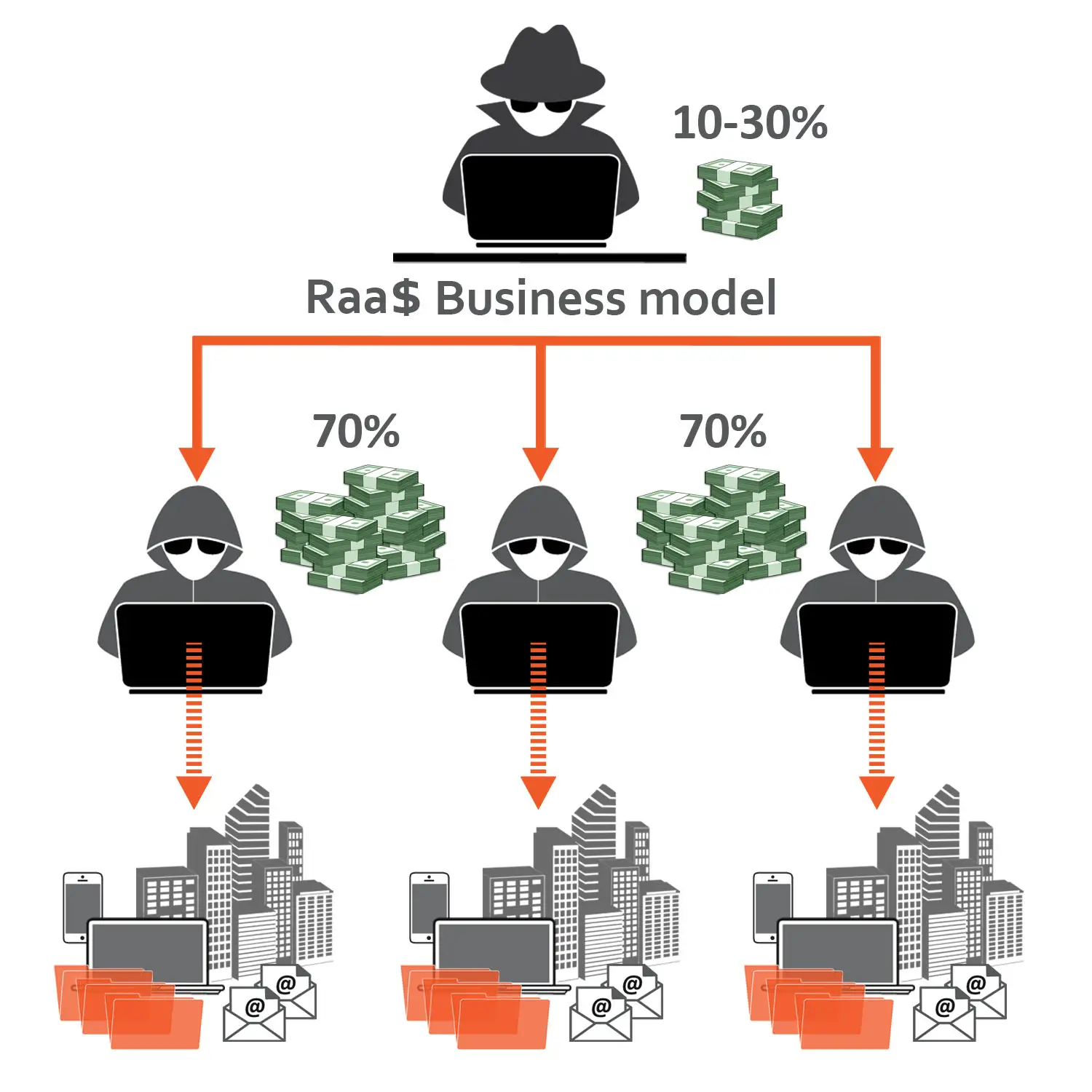
- RaaS. It’s known as “Ransomware as a Service,” and is a type of malware hosted anonymously by a hacker. These criminals handle everything from distributing the ransomware attack and collecting payments to managing decryptors — software that restores data access — in exchange for their cut of the ransom.
What are the risks of being infected?
Will take your data hostage and they can spread to all workstations connected to the same server. They can spread even to the entire Group Information System. This can lead to an infection and would result in the blocking of business activities.
Protection:
How to avoid being infected by ransomware attack:
- Do not click on suspicious links, do not open suspicious attachments
- Don’t pay the ransom: Law enforcement agencies discourage victims from paying ransom. First, there’s no guarantee that the criminals will release the user’s computer or data, and there are many examples where they didn’t, or asked for more money. If criminals will continue to receive money from these attacks, there’s no reason for them to stop.
- Do back up important data to an external hard drive
- Do update your operating system and other software.
- If they are infected disconnect your devices from the network
Here we reviewed also best computers for cybersecurity and best computer for hacking!