Phishing email attempts have been circulating for years and most IT professionals, and even a lot of end users, know about them. Yet, they continue. Why? The short answer is that they continue to work. Many end users simply don’t understand the risks and continue to respond to these e-mails. When users are educated and stop responding to the phishing, attackers will stop trying these methods (but they’re sure to try different ones). In the meantime, it’s important to educate users about the risks.
What is Phishing email?
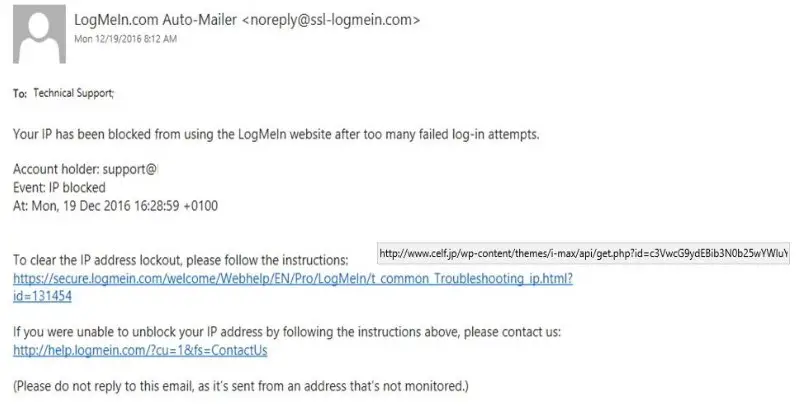
Phishing is a trapped message used to extract personal or professional confidential information (login, password), to commit fraud or install a malware on your workstation, at your expense. The e-mail may look like an official request from an employer, a public body or a large company: public treasury, bank, telephone operator etc. The message plays on psychology to make the recipient of the e-mail act and usually has several basic components:
- Impersonation
A phishing email impersonates a legitimate company. It may include actual graphics from the company and use similar fonts. For example, an email that claims it is from PayPal may include PayPal graphics.
- Identification of a problem
The e-mail usually indicates some type of problem that is of a concern to the reader. The phrase “suspicious activity” or something similar is often included in these e-mails.
- A sense of urgency
Recipients are encouraged to take immediate action. Although the phishing e-mail doesn’t state it this way, the goal is to get the user to click without any more thought.
- Dire consequences
The phishing warns of some dire consequences, such as closing an account, locking out an account, or freezing funds, if the recipient doesn’t respond. For individuals doing business through a Company such as eBay or PayPal, the threat of their account being closed, or locked, sounds dire. This often propels them into taking immediate action.
What is Spear phishing email?
Spear phishing is a variant on the phishing theme. Spear phishing attacks attempt to identify the targets. A spear phishing attack targets a specific organization or group. Recipients are more likely to open it because it looks like it’s from someone within the organization,. The contents could state something about a missed deadline and ask the user to provide some information in an attached document. The attachment includes malware and attempts to install itself on the user’s computer if the user opens it. The From address provides a level of trust because it looks like it’s coming from a fellow employee. Because of this, some users are more willing to open the e-mail and the attachment. In contrast, these users might not respond to a typical phishing attempt.
How can you detect a Phishing and a Spear Phishing?
- The context of the e-mail is not plausible or the sender is not supposed to know the e-mail address of the recipient
- The sender’s address is unknown or suspicious
- The information requested is confidential: bank details, password.
- The tone of the e-mail is threatening or plays on empathy
- The e-mail contains spelling mistakes
What are the risks of clicking on the link or opening the attachment?
You can disclose personal and confidential information to malicious people or even unintentionally install a malicious program on your computer that may infect the entire Information System.
What to do in case of phishing email?
You receive an e-mail from an unknown sender that seems suspicious:
- Avoid clicking on the link in the e-mail !
- Do not open attachments !
- If you believe this a case of phishing email, do not reply !
If in doubt, go directly to the official website to consult or modify your information
You can find more interesting examples of and spear phishing email on the following link